AWS Setup
Connecting your AWS account takes just a few clicks—whether it’s a standalone account or part of an AWS Organization. Cloudchipr generates a CloudFormation stack that automatically creates the necessary IAM roles and permissions in your environment. This enables secure cross-account access, allowing Cloudchipr to retrieve resource metadata and usage metrics from your AWS accounts.
AWS Sub-accounts auto-discovery
If you connect your AWS Organization, Cloudchipr will automatically detect all member accounts and attempt to assume roles using the default OrganizationAccountAccessRole. If this role is not present in your sub-accounts, you’ll need to create it manually as described in the Create custom roles and permissions section of this documentation.
Prerequisites
Before you begin, ensure you have the following:
- Admin permission to AWS to be able to add cross-account access IAM roles.
- If you don't have access to your AWS accounts, you can invite someone from your organization to complete the account connection for you.
Step 1: Connecting Account
Select AWS as Your Cloud Provider: Select AWS as your cloud provider on Cloudchipr and click "Next".
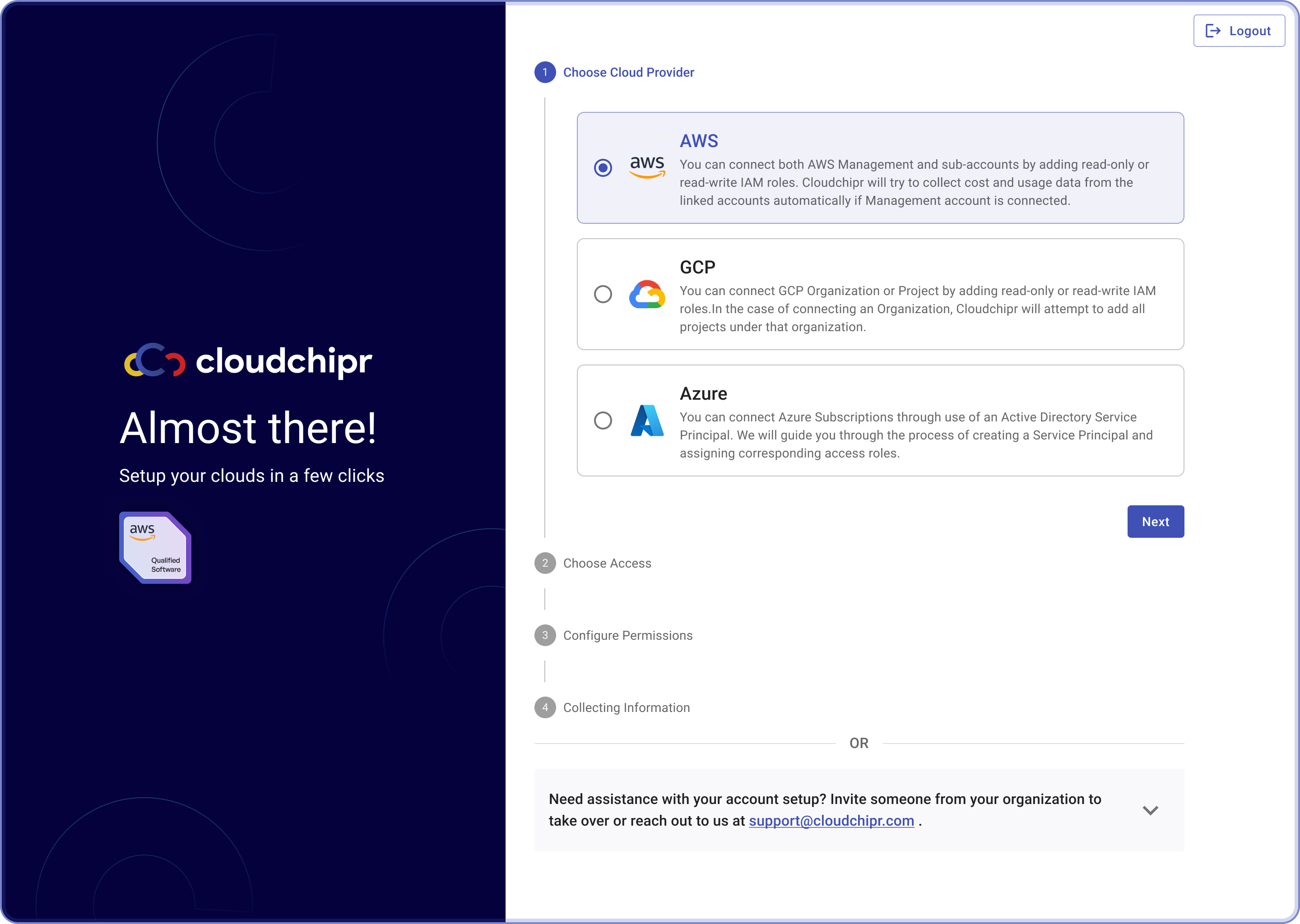
Step 2: Choose the Initial Access Mode:
Cloudchipr offers two types of access modes:
- Read/Write Access: This mode allows using automation workflows and actions. Cloudchipr will not modify any cloud resources at this stage. Confirmation will be requested before taking any action.
- Read-Only Access: Ideal for exploring cost-saving opportunities. This mode allows viewing cloud resources and sending notifications. It does not allow resource actions.
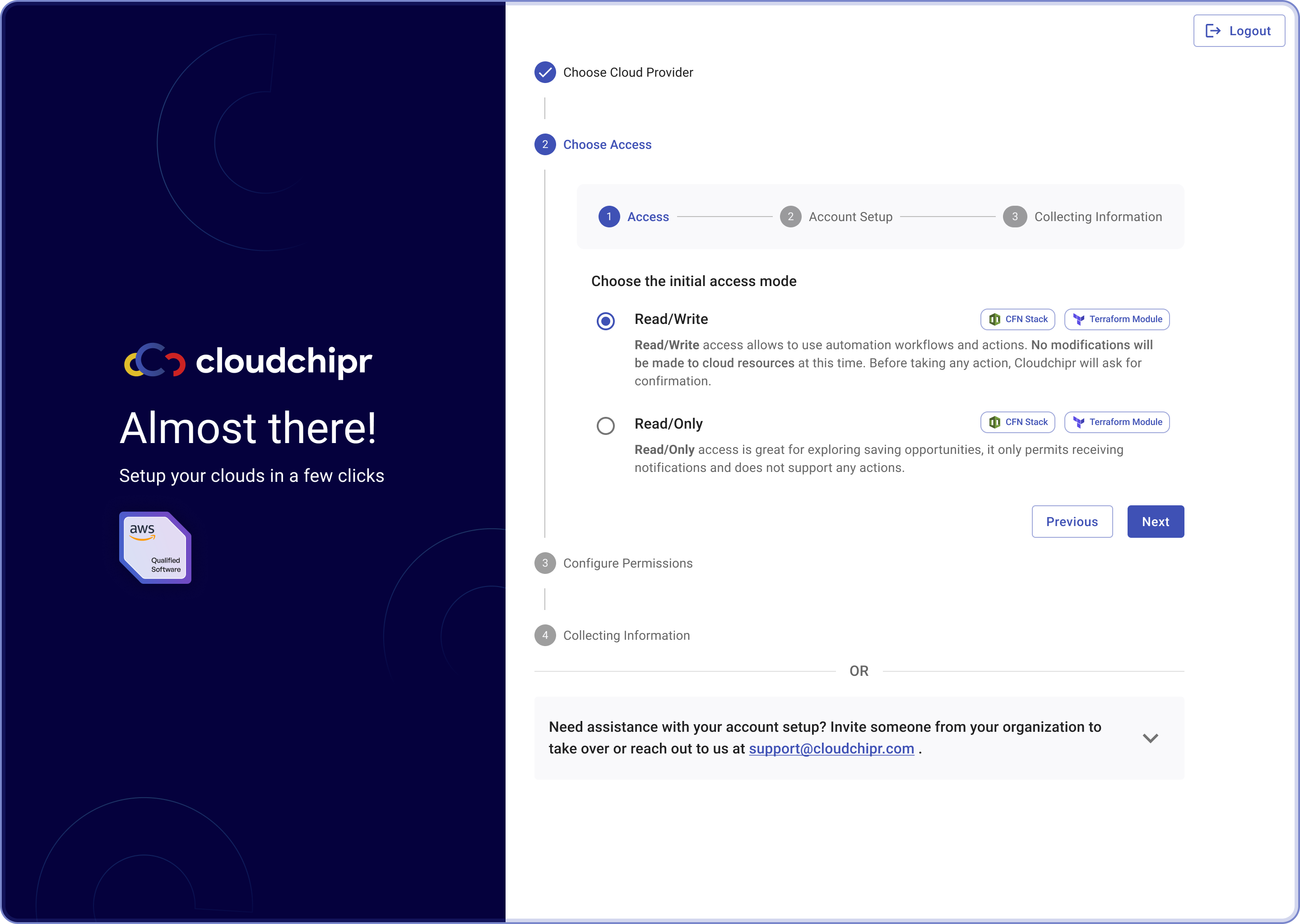
Step 3: Select Your Preferred Method for Configuring Permissions:
You can use AWS Management Console or AWS CLI to grant permissions.
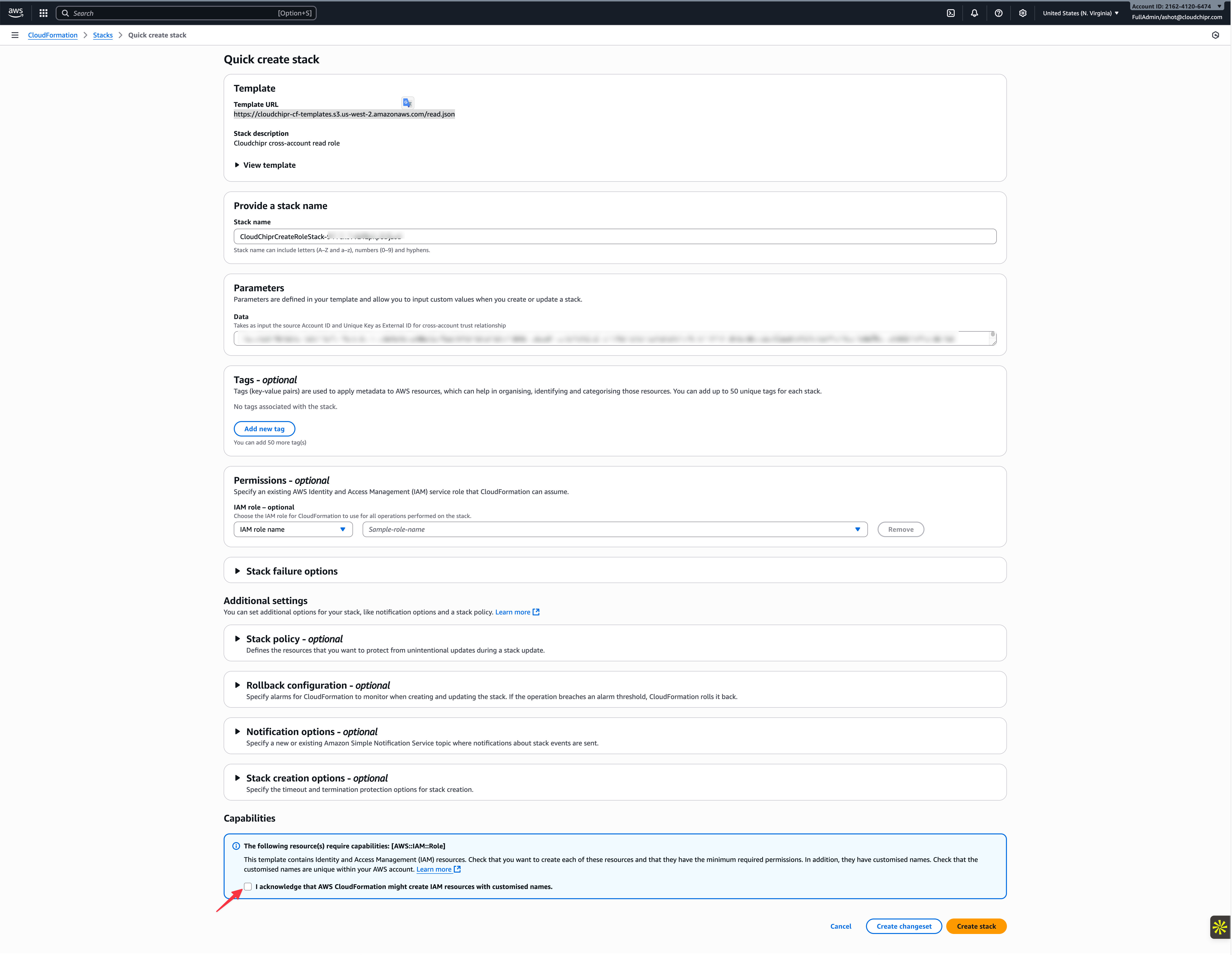
- RUN THROUGH AWS CONSOLE
- If you choose AWS Management Console, you will be redirected to your AWS account. Once you are there, please log in, verify the pre-populated values in the CloudFormation template, and create the stack.
- Acknowledge that the AWS CloudFormation template will create IAM resources and click Create Stack.
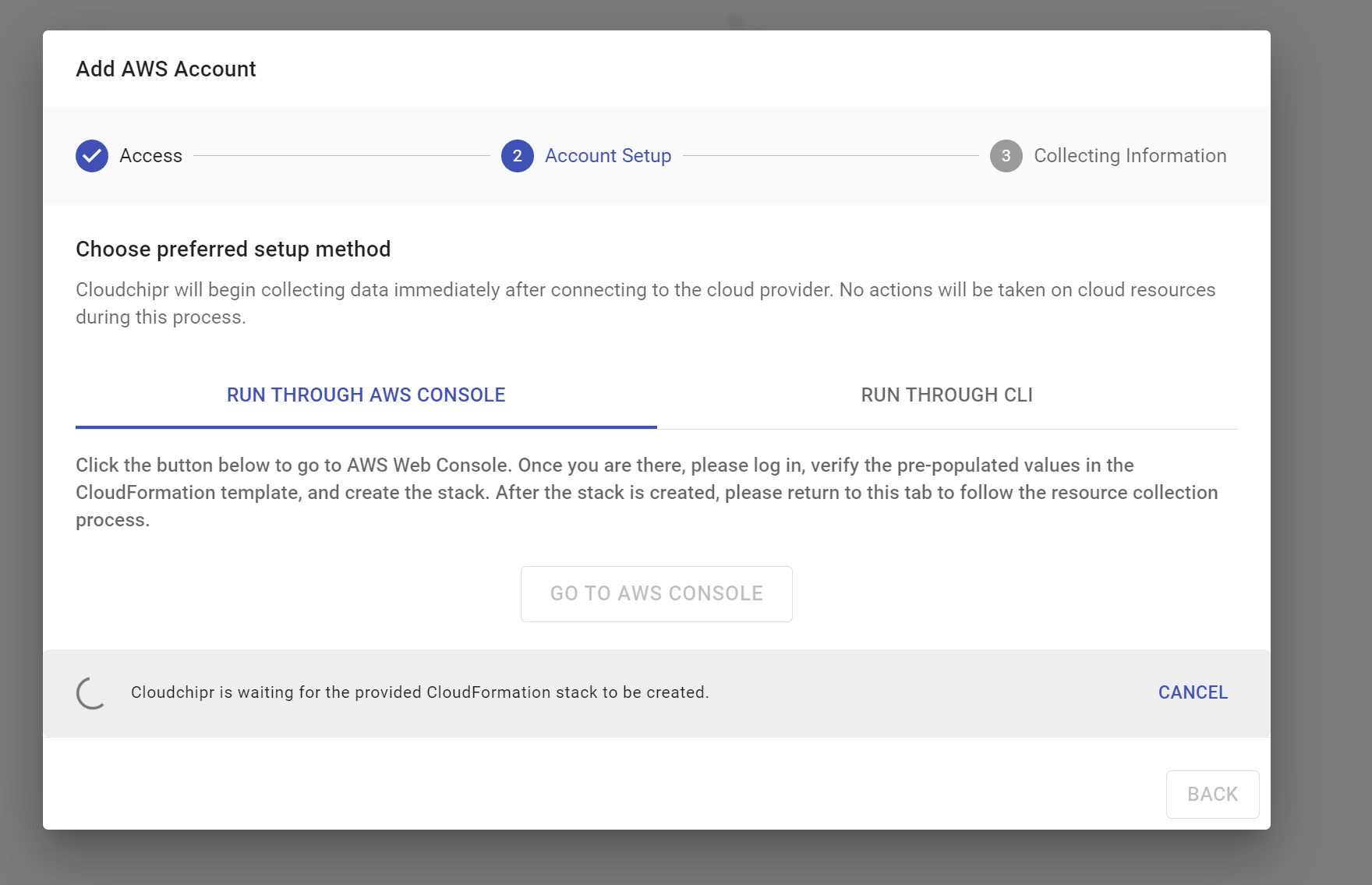
- RUN THROUGH CLI
- Before running the provided command, please make sure you have AWS CLI installed and are logged in to your desired AWS account. Then, copy and paste the provided command into your terminal and run it. Cloudchipr will monitor the progress of the stack deployment and will automatically detect when the necessary permissions are granted.
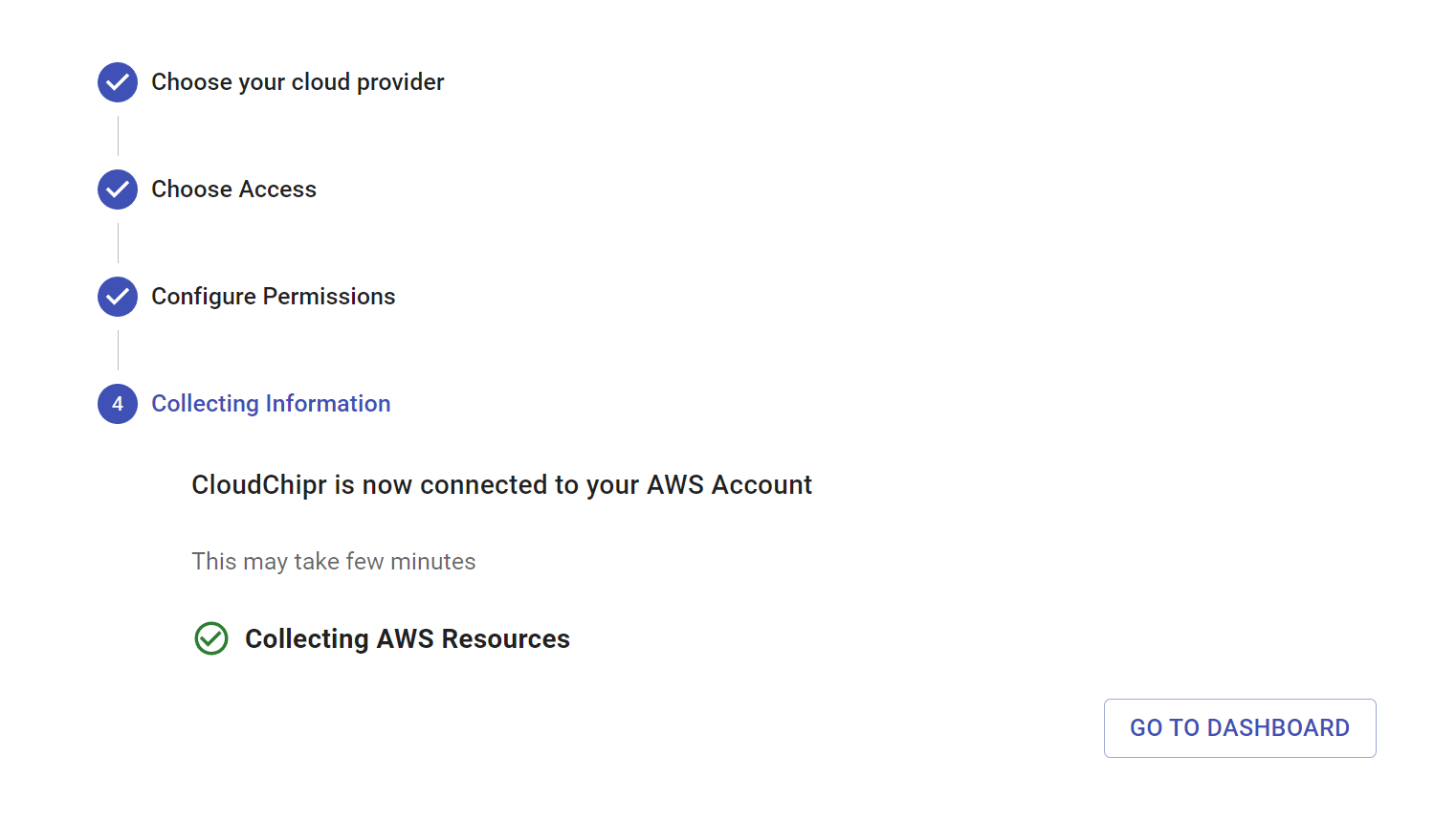
Step 4: Confirmation and Dashboard Access:
- After successful completion, a confirmation message will appear that Cloudchipr is now connected to your AWS accounts.
- Next, select GO TO DASHBOARD. This will take you directly to your Cloudchipr dashboard, where you can observe and manage your cloud costs.
Multi-region deployment (optional)
For customers who want disaster recovery for IAM roles, the same CloudFormation stack can be deployed in an additional AWS region. Cloudchipr will automatically switch to the first available region if access roles in the primary region become unavailable. This step is optional and can be safely skipped if cross-region failover is not required.
Updated 3 months ago
